Advanced and Adaptive Authentication is a technology that strengthens user authentication processes and enhances user experience. This method improves upon traditional username and password-based authentication by taking into account user habits, devices, and locations to provide a more secure authentication. Thus, it offers more effective protection against potential threats while allowing users to carry out their daily transactions more easily and seamlessly.

Adaptive Multi-Factor Authentication (AMFA) merges multiple authentication methods with smart algorithms to counter digital threats effectively, marking a significant stride in cybersecurity.
Multi-Factor Authentication (MFA) plays a vital role in compliance with various regulations, ensuring the security and integrity of sensitive data. Several regulatory standards, including but not limited to GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and PCI DSS (Payment Card Industry Data Security Standard), mandate strong authentication measures to safeguard personal, medical, and financial information. MFA, with its layered approach to user verification, aligns perfectly with these requirements, offering an extra level of defense against unauthorized access and data breaches. By implementing MFA, organizations can not only meet regulatory demands but also enhance the overall security posture of their systems and protect user privacy.


Learn how risk-based authentication tailors security measures to the perceived risk of each interaction.
Adaptive Risk Scoring
Explore how adaptive risk scoring evaluates the risk associated with each user and interaction.
Real-time Threat Analysis
Understand how real-time threat analysis helps in making instant decisions based on the risk assessment.
Discover how adaptive authentication adjusts security measures based on user behavior and risk factors.
Behavioral Biometrics:
Explore how adaptive authentication leverages behavioral biometrics to identify users based on their unique actions.
Risk-Based Authentication in Action:
Learn how risk-based authentication is integrated into adaptive authentication processes.
Delve into the advantages of advanced authentication, from improved security to enhanced user experience.
Enhanced Security: Explore how advanced authentication solutions provide a robust defense against identity theft and unauthorized access.
Seamless User Experience: Learn how advanced authentication methods can enhance the user experience by reducing friction and streamlining access.

See how adaptive authentication adapts to real-time situations with examples of its effectiveness.
Real-time Fraud Detection: Understand how adaptive authentication can detect and prevent fraud in real-time.
User-Friendly Authentication: Explore how adaptive authentication makes authentication more user-friendly while maintaining security.

Discover real-world scenarios where advanced and adaptive authentication shine in protecting sensitive data.
Secure Financial Transactions: Learn how these methods secure online financial transactions, preventing unauthorized access to accounts.
Enterprise Data Protection: Explore how organizations can safeguard their critical data and resources using advanced authentication.
Learn about key factors to consider when selecting an advanced and adaptive authentication solution.
Scalability and Integration: Understand how to choose a solution that seamlessly integrates into your existing security framework.
Compliance and Regulation: Explore how advanced authentication solutions align with industry compliance standards.

Explore how advanced and adaptive authentication address modern security challenges, such as identity theft and data breaches.
Identity Theft Prevention: Learn how these methods play a crucial role in preventing identity theft.
Data Breach Mitigation: Understand how advanced authentication can mitigate the impact of data breaches by providing an additional layer of defense.

Explore the evolution of authentication methods and the advantages of passwordless solutions.
The End of Passwords:
Learn how passwordless authentication eliminates the need for traditional passwords, enhancing security.
Seamless User Experience:
Discover how passwordless methods improve the user experience while maintaining robust security.

Learn how risk-based authentication tailors security measures to the perceived risk of each interaction.
Adaptive Risk Scoring
Explore how adaptive risk scoring evaluates the risk associated with each user and interaction.
Real-time Threat Analysis
Understand how real-time threat analysis helps in making instant decisions based on the risk assessment.

Discover how adaptive authentication adjusts security measures based on user behavior and risk factors.
Behavioral Biometrics:
Explore how adaptive authentication leverages behavioral biometrics to identify users based on their unique actions.
Risk-Based Authentication in Action:
Learn how risk-based authentication is integrated into adaptive authentication processes.

Delve into the advantages of advanced authentication, from improved security to enhanced user experience.
Enhanced Security: Explore how advanced authentication solutions provide a robust defense against identity theft and unauthorized access.
Seamless User Experience: Learn how advanced authentication methods can enhance the user experience by reducing friction and streamlining access.

See how adaptive authentication adapts to real-time situations with examples of its effectiveness.
Real-time Fraud Detection: Understand how adaptive authentication can detect and prevent fraud in real-time.
User-Friendly Authentication: Explore how adaptive authentication makes authentication more user-friendly while maintaining security.

Discover real-world scenarios where advanced and adaptive authentication shine in protecting sensitive data.
Secure Financial Transactions: Learn how these methods secure online financial transactions, preventing unauthorized access to accounts.
Enterprise Data Protection: Explore how organizations can safeguard their critical data and resources using advanced authentication.

Learn about key factors to consider when selecting an advanced and adaptive authentication solution.
Scalability and Integration: Understand how to choose a solution that seamlessly integrates into your existing security framework.
Compliance and Regulation: Explore how advanced authentication solutions align with industry compliance standards.

Explore how advanced and adaptive authentication address modern security challenges, such as identity theft and data breaches.
Identity Theft Prevention: Learn how these methods play a crucial role in preventing identity theft.
Data Breach Mitigation: Understand how advanced authentication can mitigate the impact of data breaches by providing an additional layer of defense.

Explore the evolution of authentication methods and the advantages of passwordless solutions.
The End of Passwords:
Learn how passwordless authentication eliminates the need for traditional passwords, enhancing security.
Seamless User Experience:
Discover how passwordless methods improve the user experience while maintaining robust security.
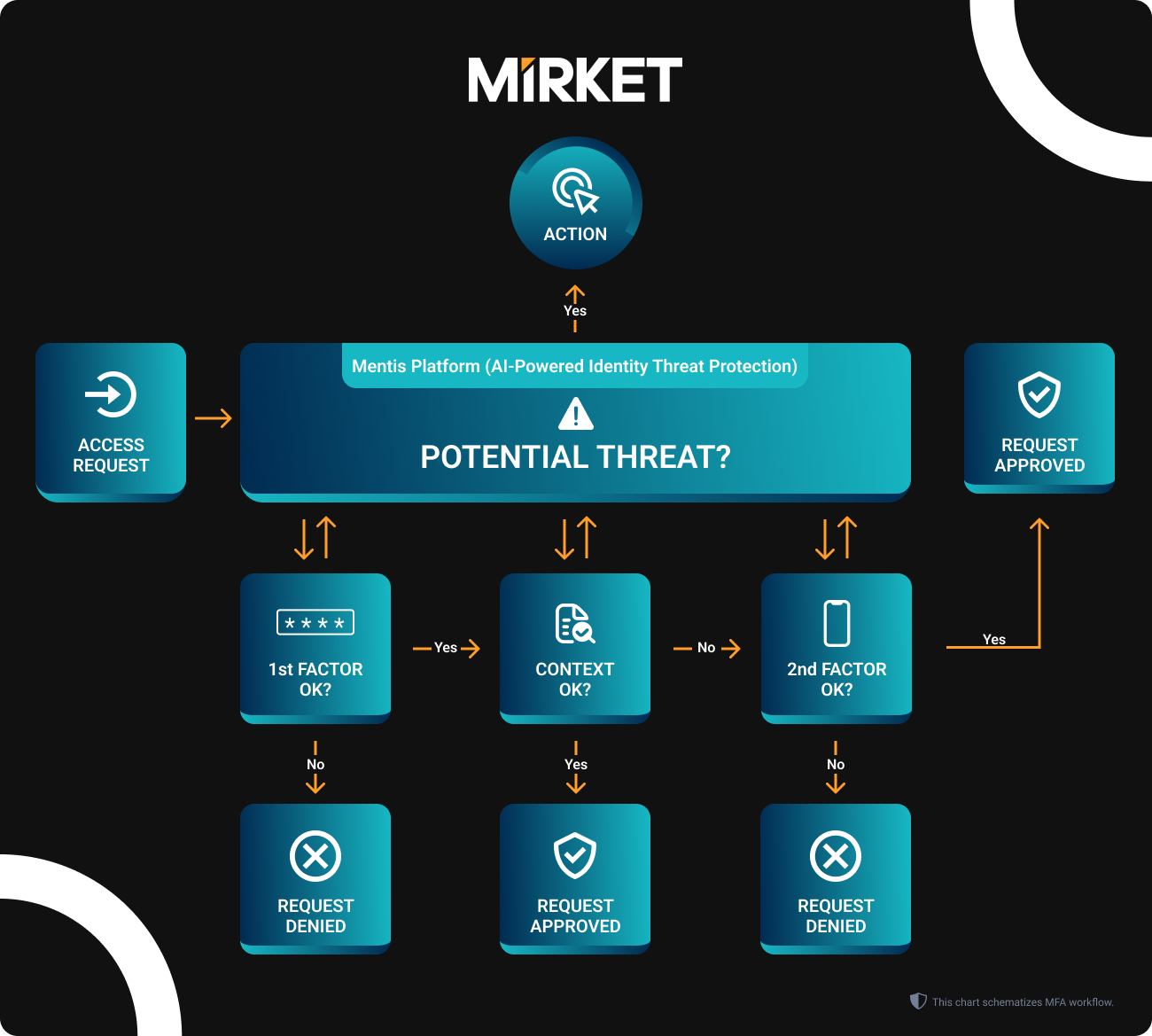
The user initiates the process by requesting access to a resource and must provide their authentication factor, typically a password (though not limited to it). With Mirket’s authentication and risk-based score-related platform, you have the flexibility to ensure more robust and user-friendly first factors
Implementing MFA everywhere, without tailoring it to the particular circumstances and potential risks, can create unnecessary obstacles. On the other hand, Mirket’s MFA policies evaluate the situation to decide if an extra layer of security is needed, thereby eliminating avoidable complications
By dynamically adjusting authentication based on risk scoring, Mirket ensures a more secure and efficient user verification process. This intelligent approach to security tailors access requirements in real-time, providing a seamless user experience without compromising on robust data protection.
Discover our comprehensive suite of products.
Ensure that all users are verified through MFA
User Empowerment, Simplified Security
Stay ahead with proactive detection and response.
Centralized identity management for streamlined access.
Discover our comprehensive suite of products.
Empowering Your Digital Trust
Unlocking Convenience, Securing Confidence
Empowering Your Defense with AI
Empower Secure Access, Simplify Control
Strengthen On-Site Protection
Mirket SAAS: Powerful, Flexible, Secure.
Security Partnerships: Unified, Scalable, Proactive
Join the Mirket family and redefine cybersecurity for businesses across the globe
Become a Partner with Mirket
Become a Partner with Mirket
Become a Partner with Mirket